Managing risk
Risk is a broad area and in the context of risk management, risk relates to threats, vulnerabilities and assets.
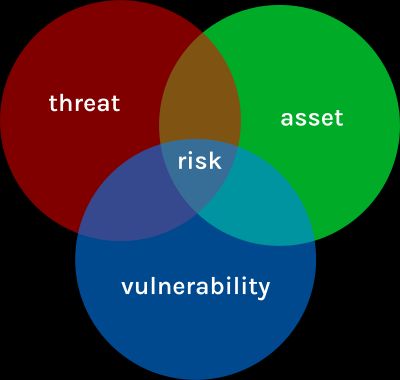
For an organization to manage risk, risk needs to be identified. Once identified, risk can be analyzed and treated.
Larger organizations manage risk by identifying as much risk at the same time while small and medium sized businesses usually start with the first risk identified.
Risk analysis is analyzing threats, vulnerabilities and assets. Threat modeling being part of threat analysis.
- Jacco Meijer
- |
- Aug 8, 2025
Data security
Data identification, data roles and data classification from a security perspective

- Jacco Meijer
- |
- Aug 15, 2025
Asset security
Information asset identification and classification from a security perspective
In risk analysis, a risk is typically evaluated by assessing two factors: likelihood and impact.
Likelihood refers to the probability that a risk event will occur, while impact represents the potential consequences or losses if the risk materializes.
The impact can be assessed in:
- quantitative terms, such as financial loss (measured in currency) or
- qualitative terms, such as the severity of the effect on project objectives (e.g., time, quality or customer satisfaction).
This approach helps prioritize risks and determine appropriate mitigation strategies.
Once inherent risk is identified and evaluated, appropriate treatment strategies are applied. These aim to reduce or manage the risk to an acceptable level. Any risk remaining after treatment is known as residual risk. The table below provides a high-level overview of common risk treatments and how they are applied.
| Evaluation | Treatment | Example Action |
|---|---|---|
| Risk exceeds acceptable threshold | Avoid | Discontinue the activity, technology or process entirely |
| Risk can be reduced cost-effectively | Mitigate | Implement technical or procedural controls |
| Mitigation is not cost-effective | Transfer | Outsource, use insurance or shift risk to cloud service |
| Mitigation and transfer are not cost-effective or feasible | Accept | Document the risk, monitor it and proceed with awareness |
Frameworks for managing risk
The ISO 31000 family is a guideline for managing risk that details a process, principles and a framework. It is a framework that fits all types of industry and is regulation independent. Many other frameworks like e.g. ISO 14971 for medical devices address specific industry types and align with industry specific regulations.
Specifically for cyber security, NIST SP 800-37 is a well known risk framework. Two other notable cyber security specific risk standards are not frameworks but do provide useful guidance.
- ISO 27005, provides guidance on managing information security risks
- NIST 800-30, a guide for conducting information security risk assessments
NIST CSF
NIST CSF, with cyber security in its name is specific for the field. It is an outcome oriented roadmap that does not mandate the how. What does NIST CSF have on the roadmap for risk management?
NIST CSF risk management
The first NIST CSF core function IDENTIFY is about the organization's current
cyber security risks. Asset management and risk management are on the roadmap
here.
The core function PROTECT is about treating the risk. Based on the results of
IDENTIFY, controls are added where needed instead of the one-size-fits-all
approach.
As expected for a cyber security framework, NIST CSF clearly has managing risk on the roadmap. But NIST CSF has a broader scope than only managing cyber security risk and the framework does not contain specifics on how to manage risk.
ISO 27001
ISO 27001 is a management system for cyber security and like NIST CSF, there is no 'how'. What does it say on risk management requirements?
ISO 27001 risk management
ISO 27001 requires 'Actions to address risks and opportunities' in clause 6 which details to:
- 6.1.2 Information security risk assessment
- 6.1.3 Information security risk treatment
Appendix A contains the recommended Information security controls and states that the controls shall be used in context with information security risk treatment (6.1.3) as mentioned above.
Two specific controls on risk management are:
- 5.7 Threat intelligence
- 5.9 Inventory of information and other associated assets
As you may expect from a cyber security management framework, ISO 27001 makes risk management mandatory. Similar to NIST CSF the standard is broader than only managing cyber security risk. Another similarity is that it does not contain specifics on how to manage risk.
Conclusion
The post below on NIST CSF and ISO 27001 states that the standards have a different purpose, but their goals align and the standards strengthen each other. This is in line with risk management being part of both standards.

- Jacco Meijer
- |
- Jun 6, 2025
Combining ISO 27001 and NIST CSF
How to use ISO 27001 and NIST Cyber Security Framework together
How to manage risk
Both standards do not mandate how to manage risk. Threat modeling is a way to achieve this. This fits on the NIST CSF roadmap and answers to the ISO 27001 requirements. More on that in the post below.
- Jacco Meijer
- |
- Jul 18, 2025
Threat modeling as part of a risk framework
Threat modeling in the context of ISO 27001 and NIST CSF