Data security
Protecting data effectively starts with knowing the data in an organization. Still a challenge for many organizations as unclear data ownership and the ongoing difficulty of proper classification continues to cause data security gaps.
The use of AI tooling still increases. Together with growing compliance demands, data classification becomes more critical than ever. Putting classification frameworks into practice however, still proves more difficult than expected. o far, only heavily regulated industries like finance and government have consistently made it a standard part of their security processes.
The field of data security is as broad as you want it to be. This post is brief and only breaks down the key roles involved in data security and the responsibilities tied to each, especially around governance and compliance.
Again, a brief view on data roles, yet essential in the field of data security, especially within larger organizations.
Data security fits within the larger scope of asset security, which deals with the systems that store, handle and transmit information. More on this in the post below.

- Jacco Meijer
- |
- Aug 15, 2025
Asset security
Information asset identification and classification from a security perspective
Data identification
Data generally grows steadily within organizations. Newly added data has significant impact on organization security which makes it important to identify new data. The more is known about the new data, the better it can be protected.
Data security roles
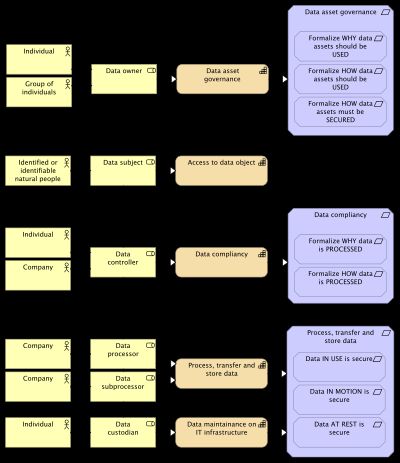
All data should have an owner to ensure proper data governance. The diagram below shows the relationship between data roles, capabilities and the relevant requirements.
The diagram uses 'data asset' to describe the value of the data. This differentiates from the actual data itself which is simply referred to as 'data'.
Data owner
The term 'data owner' is used across multiple regulations with different meanings.
- ISACA emphasizes value, quality and lifecycle governance of data, not just security
- ISO uses 'asset owner' which includes data as part of information assets
- NIST uses 'information owner' and ties the role to risk management and security authorization
This is a useful AI prompt for further research.
- create table with role usage
- each cell contains only once:
- ✅ List organizations
- ❌: Not used
- include organizations
- isaca
- iso
- nist
- columns
- data
- information
- system
- asset
- rows
- owner
- steward
- controller
- processor
- custodian
| Role \ Object | Data | Information | System | Asset |
|---|---|---|---|---|
| Owner | ✅ ISACA | ✅ NIST | ✅ NIST | ✅ ISO |
| Steward | ✅ ISACA | ✅ NIST | ❌ | ❌ |
| Controller | ✅ GDPR | ❌ | ❌ | ❌ |
| Processor | ✅ GDPR | ❌ | ❌ | ❌ |
| Custodian | ✅ ISACA & NIST | ❌ | ❌ | ❌ |
Data classification
Data classification is assigning a value and a sensitivity level based on content and context. Data categorization is grouping the classified data.
Classification is important because treating security risks for all data equally is a costly approach. It is much more efficient to classify data on sensitivity and differentiate accordingly.
Best practice
Data classification is always best practice but is usually only formalized in strongly regulated environments like military, governments and banks.
With every newly introduced cyber security law however, data classification becomes increasingly important for all organizations.
Data classification types
Data classification can be divided into three primary types.
| Classification Type | Description | Examples |
|---|---|---|
| Content-Based | Analyzes the actual data within the file or message. | Detects credit card numbers, PII or sensitive keywords in documents. |
| Context-Based | Uses metadata or environmental factors around the data. | Classifies based on file location, sender/receiver or access patterns. |
| User-Based | Relies on user roles, behavior or manual input. | User selects classification label; defaults based on department or role. |
Conclusion
Understanding data is a foundational aspect of data security. As organizations continue to generate and handle increasing volumes of data, identifying and classifying this data becomes essential for maintaining cyber security.
Assigning clear ownership and applying appropriate classification methods enables organizations to manage risks more efficiently and comply with evolving regulatory requirements.
By treating data as a valuable asset and aligning roles and responsibilities accordingly, organizations can ensure that their data governance and protection strategies are both effective and scalable.