Combining ISO 27001 and NIST CSF
The post below on NIST CSF and ISO 27001 states that the standards have different purposes, but their goals align and the standards strengthen each other.

- Jacco Meijer
- |
- Jun 6, 2025
Combining ISO 27001 and NIST CSF
How to use ISO 27001 and NIST Cyber Security Framework together
The two are relatively easy to compare and both can be used independent of jurisdiction and country. For many specific countries however, alignment with local regulations is required. This adds extra complexity to the identification of compliancy gaps. When the scope is extended from IT to OT this complexity is extended even further.
When this post mentions standards, this includes frameworks and regulations.
The table below shows a practical example of the standards that commonly need alignment in the Netherlands. The 62443 family of standards is included as an example for Operational Technology (OT).
| Standard | Description |
|---|---|
| ISO 27001 Standard | Risk based Management System standard for establishing, implementing, maintaining and continually improving Information Security. |
| ISO 27002 Standard | Supporting standard on control implementation. |
| ISA/IEC 62443 Standards | A series of standards for industrial automation and control systems (IACS) cybersecurity. |
| NIST SP 800-53 Standard | US federal standard providing a comprehensive catalog of security and privacy controls. |
| NIST CSF 2.0 Framework | Voluntary risk based outcome focused framework designed to help organizations manage and reduce cybersecurity risk. |
| NIS2 Directive | Binding EU regulation that mandates cybersecurity requirements for essential and important entities. |
| GDPR Regulation | EU regulation on data protection and privacy for all individuals within the EU and EEA. |
| BIO2 Framework/Regulation | Mandatory baseline framework aligning with ISO 27001/27002. |
Challenges
Compliancy gaps
One of the major challenges is identifying compliancy gaps and assuring all legal obligations are met. Article 20 of the NIS2 Directive for example, mandates that management bodies (e.g. board members, executives) must approve and oversee the implementation of cybersecurity risk management measures.
Consider a company that is ISO 27001 certified. This company uses the Information Security Management System (ISMS) in line with the objective of the standard. Many of the standards that need alignment have similar objectives that intersect or are subsets of the ISMS defined objectives.
Besides the possible redundant work caused by overlapping standards, the overlap introduces the risk of compliancy gaps and possible contradicting requirements.
Mapping standards
Overlapping standards and compliancy gaps cause major challenges. One of the best solutions to manage these overlapping standards are consistent and reliable mappings between the standards. These mappings are often referred to as crosswalks.
The USA based NIST organization for example, publishes many crosswalks from and to their standards.
The table below shows some of the most common crosswalks that are available for the standards in this post.
| From | To | Crosswalk source |
|---|---|---|
| ISO 27001:2022 | ISA 62443-2-1:2024 | 62443-2-1 Annex A.4, Table A.7 |
| ISO 27002:2013 | ISO 27002:2022 | ISO 27002 ANNEX B |
| ISO 27002:2022 | NIST CSF v1 | ISO 27002 ANNEX A - TAGS |
| NIST CSF v2.0 | NIST SP 800-53r5 | NIST CSF-pf-to-sp800-53r5-mappings.xlsx |
| NIST CSF v2.0 | ISA 62443-2-1:2024 | 62443-2-1 Annex A.4, Table A.9 |
| NIST SP 800-53r5 | ISO 27001:2022 | NIST.sp.800-53r5-to-iso-27001-mapping-2022-OLIR-2023-10-12-UPDATED.xlsx |
| ISA 62443-2-1:2024 | ISO 27001:2013 | 62443-2-1 Annex A.4, Table A.8 |
| ISA 62443-2-1:2024 | NIST CSF v1 | 62443-2-1 Annex A.4, Table A.10 |
| NIS2 | ISO 27001:2022 | ENISA Technical Implementation Guidance Mapping table version 1.1 |
Crosswalk spreadsheet pitfalls
For many companies it is common practice to have a spreadsheet with crosswalks between the relevant standards. As the list of standards to comply with grows, so does the spreadsheet and a growing spreadsheet can easily lead to one of the following pitfalls:
- mixing control objectives and control measures;
- lack of canonical id's;
- poor version management;
- ignoring shared responsibility in cloud contexts;
- neglecting bidirectional mappings.
Crosswalk reliability
The common pitfalls show the importance of reliable crosswalks. A good solution that ensures reliable crosswalks is the NIST IR 8477 standard. The standard is named "Developing Cybersecurity and Privacy Concept Mappings" and helps with understanding how one standard supports another and how to identify compliance gaps.
The standards achieves this by setting up an approach that is named 'Set Theory Relationship Mapping (STRM)'.
Set Theory Relationship Mapping
Definition: STRM is a relationship style derived from the branch of mathematics known as set theory. Each mapping done with this style includes both a rationale for the mapping and a relationship type.
STRM supports three options for the rationale and five relationship types for documenting the logical similarity of two concepts.
Rationale
- Syntactic: How similar is the wording?
- Semantic: How similar are the meanings of the two concepts?
- Functional: How similar are the results of executing the two concepts?
Relationship types
- Subset of
- Intersects with
- Equal
- Superset of
- No relationship
Relating the standards to risk
With the STRM approach consistent and reliable mappings can be setup between the standards. This ensures that compliancy gaps are identified and that legal obligations are met.
From here, the next challenge is to relate the objectives from all standards to the three components of risk: threats, vulnerabilities and assets.
Figure 1 from an earlier post on Enterprise Architecture models the components of risk in red and models an example of a control objective and a control measure. Both are in a group named 'Cyber security standards' which defines the the source.
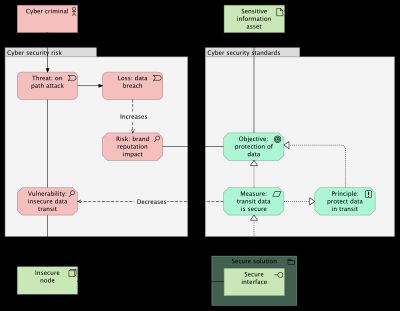
Multiple standards generally contain multiple sets of control measures and objectives. The standards in this post for example have measures defined by ISO 27002, NIST SP 800-53r5 and ISA/IEC 62443 and all standards define control objectives.
To be able to relate the components of risk in a clean and a consistent manner, a consistent set of objectives that acts as a single source of truth is required. For ISO 27001 certified organizations an obvious choice is to use the ISMS objectives as a canonical set.
Using the control objectives from ISO 27002 as a canonical set adds more granularity to the set which makes it a better fit than the objectives of the ISMS itself. The best set covers all objectives of the ISMS and has a decent amount of granularity. ISO 27002 is often a good fit, as can be e.g. NIST SP 800-53.
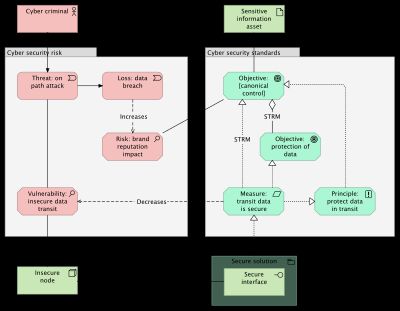
Canonical control objectives
Figure 2 shows how a canonical control objective is added. This objective aggregates the objective from figure 1 and the control measure from figure 1 realizes the canonical objective. This example shows only one control, but multiple objectives are aggregated and multiple measures realize the objective.
To ensure consistency and to identify possible compliancy gaps, all aggregation and realization relationships are documented by STRM as outlined in NIST IR 8477.
Secure Controls Framework (SCF)
Choosing a canonical set that fits is a common challenge for many companies. This challenge resulted in an open source project called Secure Controls Framework.
The framework defines a canonical set of controls and maps the set to all major standards worldwide. The advantages are obvious. Having all the mappings readily available saves a lot of work.
The framework is a good example of how the security community worldwide works together. SCF is driven by a community of experts and published as an open source project.
SCF is available as a spreadsheet and all STRM mappings are available in PDF format. A small fee is required for the STRM mappings in spreadsheet format which is a minor investment considering the gain.
Besides the canonical set of controls, SCF contains a threat catalog and a risk catalog. It defines a set of control domains which are related to 'cybersecurity & data privacy by design' principles. Another set of principles is called 'data privacy management principles' which are mapped to specific privacy frameworks.
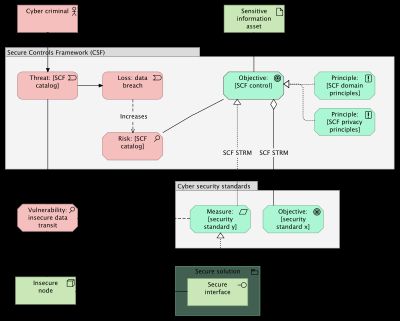
While maintaining the same high level structure as figure 1 and 2, figure 3 shows what parts are covered by SCF and how the specific SCF components relate. STRM mappings document all relationships between the canonical SCF control objective and the objectives and measures from individual standards.
The actual SCF relates threat to the canonical control. This is not modeled here because figure 3 is kept in line with figure 1 and 2. For a more in depth view on modeling with SCF, see this post on SCF and Archimate.
Other resources
The SCF solution is mentioned as an example GRC solution (Governance, Risk and
Compliance). Many other solutions exist. Leading solutions like ServiceNow,
Archer and MetricStream use proprietary schemas but align conceptually with
OSCAL or SCF for interoperability.
OSCAL: Open Security Controls Assessment Language, a NIST initiative to modernize and automate the processes of security and compliance.
Use the AI prompt below as a starter for more information on this topic.
Prompt for Cyber security data schemas
List available data schemas that capture details from security frameworks
- framework examples:
- iso27001
- nist csf
- details to capture:
- requirements
- controls
- assessments
- mappings
- output a summary table with:
- Purpose
- Key Components
- Format
- Use Case
- Open or Proprietary
Conclusion
A single canonical set of security controls can serve as a reliable source of truth amidst the growing complexity of cybersecurity standards and regulations.
Rather than treating standards as separate or competing frameworks, integrating them into one coherent control set simplifies compliancy, reduces duplication and improves manageability.
Anchoring a security program into a single, well-structured set of controls ensures consistent implementation, efficient audits and alignment with both international best practices and national regulations.
The post below on canonical controls explores in more depth how to use the SCF canonical control objectives with Enterprise Risk and Security Management (ERSM) in Archimate.

- Jacco Meijer
- |
- Oct 14, 2025
Canonical controls with Enterprise Risk and Security Management
How to use the SCF canonical control objectives with ERSM in Archimate
- Jacco Meijer
- |
- Jul 25, 2025
Threat modeling, security frameworks and Enterprise Architecture
Combining ISO 27001, NIST CSF and threat modeling with Enterprise Architecture strengthens all elements