Secure Controls Framework
The post below on how to align the steadily increasing number of security standards refers to the Secure Controls Framework (SCF) as an example. This post is about how to use the SCF canonical control objectives with Enterprise Risk and Security Management (ERSM) in Archimate.
- Jacco Meijer
- |
- Oct 7, 2025
ISO 27000, ISA 62443, NIS2, BIO, NIST CSF and NIST SP 800-53
How to align the steadily increasing number of cyber security frameworks, standards and regulations?
Setup SCF
Using the SCF can save a lot of time because it brings ready to use STRM relationship documentation and it improves in terms of efficiency, but SCF is not a commercial off the shelf solution. Because frequent misunderstanding, SCF provides what the SCF is not in the official documentation. In summary:
NOTA substitute for performing due diligence and due care,NOTA complete technology or documentation solution to address all your cybersecurity & data privacy needs andNOTA solution guaranteed to meet every compliance requirement of your organization
SCF has extensive documentation on setting up a Cybersecurity & Data Privacy Risk Management Model. Before assessing the likelihood and impact of risk in detail it requires in depth risk analysis first. This includes setting up risk, threat and controls catalogs.
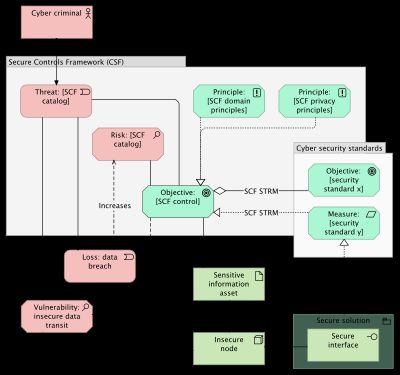
SCF Meta model
Figure 3 in this post on security standards models all elements of the SCF.
Figure 1 shows an updated version of the same model with some changes:
- all technology elements are moved together;
- the threat catalog is linked to the SCF control;
- the loss element, representing the likelihood that the risk occurs is moved outside of the SCF
Modeling risk and security
In risk analysis, a risk is typically evaluated by assessing two factors: likelihood and impact.
Likelihood refers to the probability that a risk event will occur, while impact represents the potential consequences or losses if the risk materializes.
Adding threats and vulnerability to assets modeled in Enterprise Architecture is a good way to understand risk. Especially for complex risk, visualizing the relationships helps assessing risk.
When inherent risk is evaluated and likelihood or impact can be reduced with cost effective measures the canonical controls come into play. The table below shows other possible risk evaluation outcomes.
| Evaluation | Treatment | Example Action |
|---|---|---|
| Risk exceeds acceptable threshold | Avoid | Discontinue the activity, technology or process entirely |
| Risk can be reduced cost-effectively | Mitigate | Implement technical or procedural controls |
| Mitigation is not cost-effective | Transfer | Outsource, use insurance or shift risk to cloud service |
| Mitigation and transfer are not cost-effective or feasible | Accept | Document the risk, monitor it and proceed with awareness |
Archimate modeling with SCF
Modeling archimate with SCF requires the SCF components to be available as archimate elements. Figure 1 shows that these components are:
- the threat catalog;
- the risk catalog;
- the principle sets;
- the SCF control objectives.
When the catalog solution and the archimate model solution are not the same, interfacing is needed to make the catalog available to the model solution.
For example, the Bizzdesign model solution is able to interface with the IT management platform ServiceNow. Another example on the Bizzdesign platform is setting up an Excel connector.
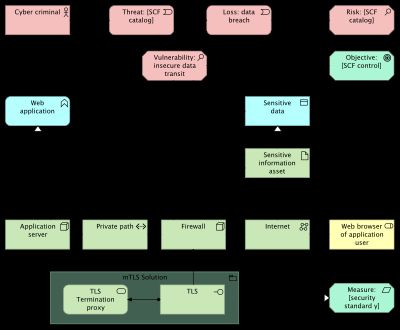
Example model
Figure 2 shows an archimate model of a simple web application that uses SCF to model risk.
This view leaves out the principle sets as well as many of the SCF internal relationships as modeled in figure 1. The view focuses on these elements:
- Loss: connects threat and risk, the loss event represents the probability that the threat event exploits the vulnerability;
- Vulnerability: connects the elements that contain the weakness with the threat and relates the threat to the SCF objective.
- Measure: is realized by the technology elements that secure the vulnerability.
Cyber security standards
Figure 1 shows control measures from standard y and control objectives from standard x. This is to illustrate that some security standards contain mainly objectives, like ISO 27001 and NIST CSF 2.0. Whereas other standards contain merely measures. ISO 27002 and NIST SP 800 53 are good examples of the latter.
The example in figure 2 uses a control measure. The measure is realized by the mTLS solution. Depending on the use case, the choice is to either use the measure from the standard or to leave the measure out and have the mTLS solution realize the SCF control objective directly.
Same choice for the influence relationship that decreases the vulnerability. This can be modeled from the control objective, the control measure or both.
For risk assessment both choices make little difference. Depending on an audit for a specific standard you might need to model accordingly. Think of the evaluation of which measures from a standard have a realized-by relationship.
Traffic lights and heat maps
Some Enterprise Architecture solutions have integrated risk properties like vulnerability level and threat capability for qualitative risk analysis. These property values are often displayed as traffic lights next to the Archimate elements.
Evaluating risk with properties allows for e.g. security heat map representations.
Conclusion
This short post is mainly about the two example models. Figure 1 can be used as a SCF meta model and figure 2 shows how to add risk assessment and risk treatment.
The models in this post are kept simple and risk management for these models is mainly overkill. For organizations that use the holistic security approach however, models like these add great value.

- Jacco Meijer
- |
- Oct 7, 2025
ISO 27000, ISA 62443, NIS2, BIO, NIST CSF and NIST SP 800-53
How to align the steadily increasing number of cyber security frameworks, standards and regulations?
- Jacco Meijer
- |
- Jul 25, 2025
Threat modeling, security frameworks and Enterprise Architecture
Combining ISO 27001, NIST CSF and threat modeling with Enterprise Architecture strengthens all elements