NIST CSF
The post below about combining ISO 27001 and NIST CSF shows an Enterprise Architecture (EA) model that maps the two standards. This post is about how security principles can be added.

- Jacco Meijer
- |
- Jun 6, 2025
Combining ISO 27001 and NIST CSF
How to use ISO 27001 and NIST Cyber Security Framework together
Example set of security principles
Without elaborating on the source of the set, this post uses the set of security principles below as an example.
- Defense in depth
- Keep it simple
- Leveraging existing components
- Privacy by design
- Secure by default
- Secure by design
- Separation of duties
- Zero trust
Principles by TOGAF
The Open Group maintains a Framework for EA known as TOGAF. This framework gives a clear and very useful definition of a principle.
Using the TOGAF definition of a principle in a simple AI prompt, the hard work of defining proper principles becomes less of a burden. Principles are fully text based with little logic which results in only a few hallucinations.
Correcting them is fairly easy for a skilled professional. The prompt below is a good way to start.
Define for security principle “Defense in depth”:
- Documentation
- the fundamental rule
- Implications
- the business requirements for carrying out the principle in terms of resources, costs and tasks
- the IT requirements for carrying out the principle in terms of resources, costs and tasks
- possible incongruent systems upon principle adoption
- possible incongruent standards upon principle adoption
- possible incongruent practices upon principle adoption
- Rationale
- the business benefits of adhering to the principle, using business terminology
- the similarity to the principles governing business operations
- the relationship to other principles and the intentions regarding a balanced interpretation
- the situations where one principle would be given precedence or carry more weight than another
EA Capabilities
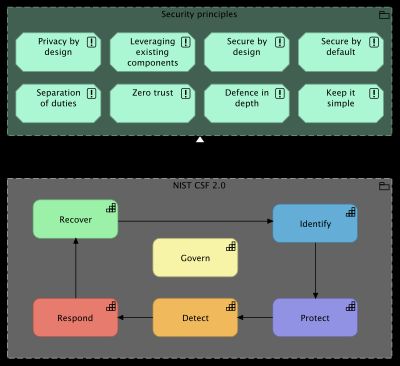
The post on combining ISO and NIST refers to NIST CSF core functions as EA capabilities. Using these capabilities to realize the security principles results in the simple conclusion that the full NIST CSF adds to all of the security principles.
It is possible to split the NIST CSF core functions into prevention, detection and reaction but the conclusion remains the same.
Security controls
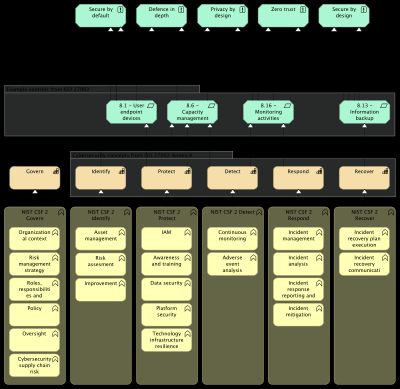
Having security controls realize the security principles is far more useful than have the EA capabilities realize the principles. The model below shows an example. Five security principles are realized by four security measures. The rest of the model is taken from the post on combining ISO and NIST.
All in one the model shows how EA business functions contribute to realizing security principles. For simplicity only four ISO controls are shown and the EA capabilities sit in between the EA business functions and the ISO controls.
As mentioned in the post on combining ISO and NIST, it makes sense to directly map each business function to one or more ISO 27002 controls.
The model shows ISO controls and (of course) NIST SP 800-53 controls can be modeled in the same way
Conclusion
AI can be of great help when setting up security principles and realizing principles by security controls tell how useful the principles are.
Most security principles have broad meaning and do not only help in realizing controls. A principle like e.g. 'secure by design' helps in the broad way the principle was intended.
Adding principles to EA adds to understanding security. Especially for security principles it is a good way of sharing knowledge and creating awareness on the – steadily growing – field of EA security.
Archimate security elements
For reference, the Archimate 'Control Measure' and 'Security Principle' elements are explained in the post blow.

- Jacco Meijer
- |
- Jun 20, 2025
Archimate risk assessment elements
A few simple specializations for working with risk assessments in Archimate