Threat modeling roots
Threat modeling has it roots in organizations that needed to manage risk. At first this was mainly military strategy and software engineering and over time it formalized within the field of cyber security.
Risk frameworks
Threat modeling is part of the broader scope 'managing risk'. Two of the most trusted cyber security frameworks describe risk management as an essential part of cyber security but these frameworks do not describe the 'how'. More on those frameworks in the post below.
Threat modeling on the other hand is all about the 'how'. It is a set of methods, techniques and tools that help managing risk in a practical way. The practical nature of the field make that threat modeling often is referred to as a culture.
Threat modeling is a natural fit for ISO 27001 and NIST CSF as it contributes to managing risk.

- Jacco Meijer
- |
- Jul 11, 2025
Cyber security risk frameworks
Managing cyber security risk with ISO 27001 and NIST CSF
Threat modeling culture
Back in 2007 when devOps found its way into the world, the adoption of the idea was often referred to as a culture shift. From separate silo's to an integrated process.
For threat modeling the culture shift is from upfront security risk assessment to the awareness that risk assessment is a continuous process that ideally lives within the Systems Development Life Cycle (SDLC).
Attack surface challenges
Frequent threats on a large attack surfaces make managing the imposed risks a challenge. Challenging for small and medium businesses and an even more for governments and larger enterprises.
The observatory nature of threat modeling helps with these challenges. Risk assessment as a continuous process makes risk management much more efficient and the collaborative nature of threat modeling improve the quality of the assessments.
Threat modeling methods
MITRE ATT&CK
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations.
STRIDE method
STRIDE was developed by Microsoft in the 90s and is a useful classification system for grouping threats.
PASTA method
PASTA is an abbreviation for Process for Attack Simulation and Threat Analysis.
The method uses the attacker perspective as a starting point and combines business goals with a technical scope. The structured method can be repeated which makes it suitable for industries where compliance is key.
Other methods
Use this AI-prompt to get started and customize where needed.
Create a matrix:
- conditions:
- output on screen csv
- use ✅ for yes
- use ❌ for no
- use 🟠 for partial
- add clarification to every icon, avoid comma’s
- horizontal: include all known threat modeling methods
- vertical:
- vendor or source
- main focus
- is proprietary or open source
- data as a major asset
- attacker-centric or asset-centric or system-centric
- techniques
- tools
Threat modeling techniques
Common techniques for threat modeling include the start perspective, using a spreadsheet and using a whiteboard.
Start perspective
Depending on the context threats are commonly defined by starting with one of these three perspectives.
| Perspective | Starting point for identifying threats |
|---|---|
| Attacker | Setup a motivation stack for possible attackers |
| Asset | Classify assets by determining quantitative and qualitative asset value |
| Software | Visualize components, processes and data flows |
Spreadsheet technique
A classic approach to threat modeling is the spreadsheet exercise. Simply add the components of risk, as mentioned at the start of this post, to the columns of a spreadsheet and fill the rows with possible threats and risk treatments.
From spreadsheets it's a small step to a more structured approach using specific tooling. From there integration with Enterprise Architecture as a next step is a way to reach the holistic view on security risk.
Whiteboard technique
More in depth is the whiteboard approach where developers, IT architects and stakeholders together identify threats and compose possible treatments. Once a threat is identified on the whiteboard, the threat can be formalized and documented by adding the threat to Enterprise Architecture.
Specific tradeoffs of treatments are added and updated when situations change.
Threat modeling tools
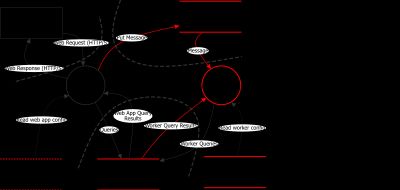
Many threat modeling tools exist. Below an example threat model distributed with the free OWASP Threat Dragon tool.
Tooling can help, but a threat modeling culture should be the main goal.
KPIs
Common practice for threat modeling is KPI monitoring. Because true value is in the culture a good indicator is job satisfaction for roles involved in threat modeling. Of course, many other obvious metrics can be monitored.
Conclusion
Threat modeling is a good fit for both ISO 27001 and NIST CSF standards. It provides the context based risk management described by both standards.
The standards describe that managing security risks is a collaborative effort and how this should be a foundational element of an organization. This collaborative effort is at the core of the threat modeling culture.
Strengthen with Enterprise Architecture
Combining ISO 27001, NIST CSF and threat modeling with Enterprise Architecture strengthens all elements. More on that in the post below.
- Jacco Meijer
- |
- Jul 25, 2025
Threat modeling, security frameworks and Enterprise Architecture
Combining ISO 27001, NIST CSF and threat modeling with Enterprise Architecture strengthens all elements