Earlier posts
This post ties together three earlier posts on security frameworks and threat modeling by using the frameworks and threat modeling in Enterprise Architecture (EA).

- Jacco Meijer
- |
- Jun 6, 2025
Combining ISO 27001 and NIST CSF
How to use ISO 27001 and NIST Cyber Security Framework together

- Jacco Meijer
- |
- Jul 11, 2025
Cyber security risk frameworks
Managing cyber security risk with ISO 27001 and NIST CSF
- Jacco Meijer
- |
- Jul 18, 2025
Threat modeling as part of a risk framework
Threat modeling in the context of ISO 27001 and NIST CSF
Conclusions from earlier posts
- ISO 27001 and NIST CSF can reliably be used together and risk management is an essential part of both
- Both standards do not mandate how to manage risk
- Threat modeling is a way to achieve the context based risk management described by both standards
- The standards describe that managing security risks is a collaborative effort and how this should be a foundational element of an organization. This collaborative effort is at the core of the threat modeling culture.
Enterprise Architecture (EA)
Both the observatory nature of threat modeling and the holistic nature of Enterprise Architecture contribute to improved risk management.
Threat modeling helps by collaboratively modeling new threats and treatments. EA helps by relating the components of risk to the holistic view of the enterprise.
Observing and modeling risks related to motivation, strategy, business goals, the application landscape and the technology used, is an enormous strength.
Open Agile Architecture (O-AA)
Technology changes, threats change, EA should change accordingly. Because of the growing need for enterprise agility in the digital age The Open Group introduced Open Agile Architecture late 2020.
EA in a threat modeling culture
A threat modeling culture combined with EA adds to awareness and to formally sharing security details. It adds to consistent methods and when threat modeling becomes part of the Systems Development Life Cycle (SDLC) threat modeling adds to the feedback loop as described in the fourth NIST CSF tier.
Studying all four NIST CSF tiers closely shows that threat modeling increases cyber security by adding maturity to all four tiers.

- Jacco Meijer
- |
- Jun 27, 2025
NIST CSF Tiers for cyber security risk governance and management
NIST CSF 2.0 contains useful tiers for Capability Maturity Modeling in Enterprise Architecture
Enterprise Risk and Security Management (ERSM)
The strength of Archimate (3.2 Specification) is in the layers and the 60 elements. The six layers enable modeling a holistic view of an enterprise.
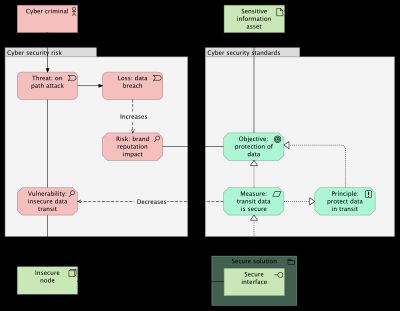
Figure 1 shows an Archimate model for modeling risk.
Cyber security risk
The three components of risk are modeled in red:
- threat (business event);
- vulnerability (assessment);
- loss (business event), risk is the likelihood of this loss.
Cyber security standards
The cyber security standards group shows the defense as defined by a security standard:
- one of the objectives of a security standard;
- one of the control measures as defined by a security standard;
- a global security principle.
Technology layer
Around the groups are three technology elements:
- Sensitive information asset, protected by a control objective;
- Insecure node, part of the infrastructure that contains a vulnerability;
- Secure interface, as part of a secure solution that realizes one of the control measures.
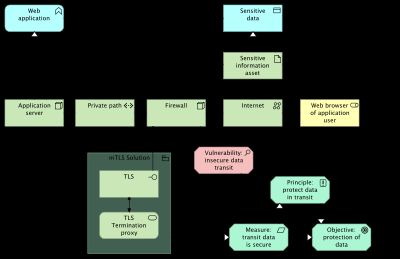
With the risk defined, the vulnerability element can be used to model risk by associating the element to any of the 60 Archimate elements. Figure 2 shows an example where the firewall contains the vulnerability.
This example uses the technology layer to model the risk, but other layers are equally useful. The application layer for example, can be used to model vulnerabilities in application functions and a vulnerability in a business process as another example, can be modeled on the business layer.
ABB and SBB as defined by TOGAF maintained by The Open Group
Risk assessment elements
The diagram uses risk assessment elements as outlined in the post below.

- Jacco Meijer
- |
- Jun 20, 2025
Archimate risk assessment elements
A few simple specializations for working with risk assessments in Archimate
Conclusion
Threat modeling helps by collaboratively modeling new threats and treatments. The holistic view EA provides helps by relating the components of risk to motivation, business goals, the application landscape and the technologies in use.
The post below details all 60 Archimate (3.2 Specification) elements which all can be used to model risk. That way, a modeled holistic view of an enterprise becomes even more valuable than it already was.
Fast moving technology introducing new threats constantly asks for architecture agility. Hence the reference to Open Agile Architecture in this post.

- Jacco Meijer
- |
- Mar 18, 2025
Visualizing IT Architecture in three languages, UML, C4 and ArchiMate
What are the differences and what are these languages most used for?
- Jacco Meijer
- |
- Oct 7, 2025
ISO 27000, ISA 62443, NIS2, BIO, NIST CSF and NIST SP 800-53
How to align the steadily increasing number of cyber security frameworks, standards and regulations?