DRAFT
Threat modeling
Threat modeling originates from organizations that need to manage risk. To understand the context of threat modeling and how it fits into ISO 27001 and NIST CSF the concept of managing risk needs to be clear.
Managing risk
Risk is a broad area and in this context risk relates to threats, vulnerabilities and assets.
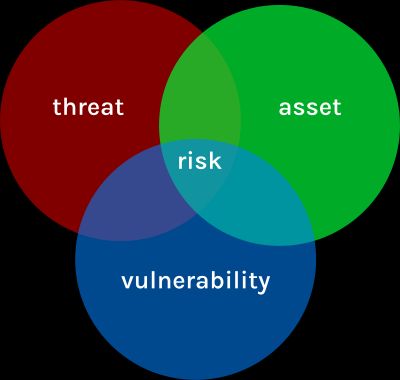
For an organization to manage risk, risks needs to be identified. Once risks are known and classified risk is analyzed in depth.
Larger organizations will manage risk by identifying as much risks at the same time while small and medium sized businesses often start with the first risk that is identified.
For risk analysis the image above is used and threats, vulnerabilities and assets are all analyzed. Threat modeling being part of the threats analysis.
With this in depth analysis, risk is evaluated by looking at the likelihood and the impact of the risk. Likelihood is the probability that a threat exploits a vulnerability and impact is the possible asset value loss. In a quantitative way when measured in currency and in a qualitative way when evaluating importance.
Once inherent risk is evaluated, it can be treated and residual risk remains. The table below shows the high over view of this process.
| Evaluation | Treatment | How |
|---|---|---|
| Risk exceeds a threshold | Avoid | Stop using a specific technology or behavior |
| Likelihood or impact can be reduced with cost effective measures | Mitigate | Implement controls |
| Mitigation is not cost effective | Transfer | Shift risk onto a 3rd party by e.g. insurance or cloud services |
| Mitigation and transfer are not cost effective | Accept | Be aware |
Frameworks for managing risk
TBW
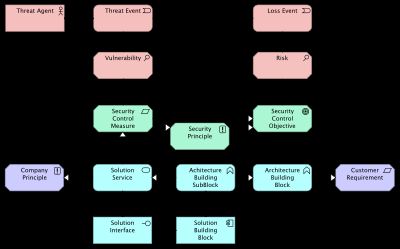
Threat modeling meta model